 “It is a very sad thing that nowadays there is so little useless information.” - Oscar Wilde
“It is a very sad thing that nowadays there is so little useless information.” - Oscar Wilde
The world is a growing resource. No disrespect to Oscar Wilde, but yesterday’s useless information is essential data today, and that is by no means a sad thing.
When it comes to collecting useful information, the “Internet of Things” (IoT) has eradicated nearly all of the limitations previously posed by geographic and political barriers. First coined by British entrepreneur Kevin Ashton in 1999, the IoT is a network of physical devices such as smartphones, vehicles, buildings, homes and other items embedded with electronics, software and sensors that enable the collection and exchange of data. We are now worldwide consumers seeking products, employment, entertainment and information through personal devices and applications that easily integrate the physical world into a giant network of connected “things.” Some experts estimate that the IoT will consist of 50-75 billion objects by 2020.
Today, the IoT is widely used as a marketing platform. Businesses connect with consumers by creatively exploiting information made available by the IoT and using geo-fencing techniques. Geo-fencing is technology that uses GPS to define a virtual boundary, or “fence,” to be put around any location or combination of locations. By setting alerts to track social media activity for specific keywords in user comments or postings, businesses can identify you – the consumer, what you consume, and where you consume it. Data extrapolated and aggregated from your past purchases can be used to sell you new products.
Conceptually, this sounds a lot like what George Orwell warned us against back in 1949 with the publication of his seminal work, “1984.” However, even Orwell couldn’t fathom a communications platform as vast, convenient and embraced as our internet.
Marketing advantages aside, this vast network of information has become an invaluable tool for law enforcement and national defense agencies. Data obtained from these networks can be used to identify and evaluate actions and behavior patterns within crime-ridden neighborhoods and global areas of conflict, allowing for the implementation of proactive solutions to resolve situations before they escalate.
Geo-fencing technology has now found its way into the realm of insurance investigations. With more ease than ever, special investigation teams can utilize this technology as a tool to aggregate location-based intelligence data for analysis to assist in claims investigation and resolution.
Unlike telephone conversations, social media posts are an example of “open source” communications. As such, this information is public and can be tracked. Existing historical posts can be collected. Alerts can be set up to send a notice when a person of interest is actively posting or communicating. Upon review of these public communications, investigation strategies can be more narrowly focused with significantly less uncertainty.
Image recognition technology is also making its way into the special investigation toolbox. This technology utilizes artificial intelligence and machine learning to understand the properties of images. These complex recognition programs can detect and identify an object or feature within a digital image or video.
Hotels and casinos have employed facial recognition software for years. You might recall that impressive concierge who remembered your name a year after your previous visit. Sorry, but you may not have been as memorable as you were led to believe. Wish you had that $10 tip back now?
The power of combining image recognition algorithms with geolocation are exemplified in movies like “The Bourne Identity” where a fractional portion of a facial image is used to locate a target on the other side of the globe.
Image recognition techniques are not just limited to the identification and location of faces. Aggregated data files also include landmarks, buildings, terrain, sounds, voices and vehicles – all stored in information “warehouses” for immediate and future use.
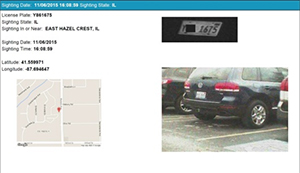
One such information warehouse is particularly useful in claims investigations. License plate recognition technology, known as Vehicle Sightings, utilizes a national system of fixed and mobile camera units to capture license plate images. The images are compiled in a database and integrated with online mapping tools to provide documented vehicle sightings, which confirm the vehicle’s identity, time and date of the sighting, and the geolocation. The database contains billions of vehicle plate images and can be an effective tool for auto claim investigations. It can also be used in conjunction with skip traces, and may be useful in identifying potential employment and activity trends.
There are already several billion image files readily accessible today and tens of millions more are being added daily. By comparison, after decades of accumulation, fingerprints on file worldwide only number about 100 million. Accessing the database and employing social media and recognition applications adds an entirely new dimension to investigative services such as witness identification, skip traces and surveillance operations. Accident scenes are now on center stage. Actionable intelligence is being gathered and distributed by unwitting collaborators. Smartphones just need to be aimed. Who can resist taking a few quick pics of an unfortunate event to share with the world? Vacation pictures and videos are now being used to determine causation and liability.
While this may all seem alarming as it relates to privacy, everything described here is a matter of public record. For those committing criminal and fraudulent activities, geolocation and data recognition techniques can likely leave clues to their misdeeds. It should be mentioned that criminals in turn are capable of taking public information that you may be sharing and use it against you, so please take appropriate steps to protect your own data.
Those who commit insurance fraud cost businesses and consumers billions of dollars every year. Utilizing the technology and data available today can contribute to cost savings in the long term. Sedgwick’s special investigation unit (SIU) works diligently to use the resources and tools at our disposal to address insurance fraud matters through prevention, detection, investigation and mitigation while always adhering to established laws and federal and state guidelines.
I welcome your comments and thoughts on how these and other emerging technologies might benefit claim investigations.
Michael Anderson, Director of Claims, SIU Operations, Sedgwick